Easy Auth Using X Ms Token Aad Access Token As A Bearer Token
- 17 Jan 2020
EasyAuth (https://cgillum.tech/category/easy-auth/) generates an internal access token ‘x-ms-token-aad-access-token‘. By default this token is an internal only format that you can’t use as a bearer token (it does not even look like one). You can utilize an unpublished (until now) feature to authenticate against another resource and this will result in a bearer token being generated that you can use to access that resource. The concept is that you can add additional login parameters that authenticate you against the object you wish to get an access token for. So you log into that resource and an access token is generated for you by Easy Auth. Special thanks to Connor McMahon who helped me get this all figured out!
Walkthrough
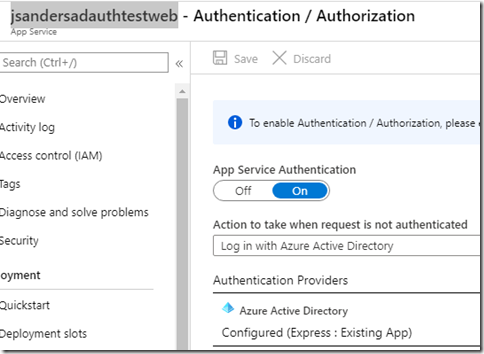
In this example, An app called “jsandersadauthtestweb” and will be the app that will be used to authenticate and will in turn use a bearer token to authenticate to the api app called “jsandersadtestapi”
Create an App Service and use the Authentication Active Directory express mode to generate the necessary entries in your Active Directory.
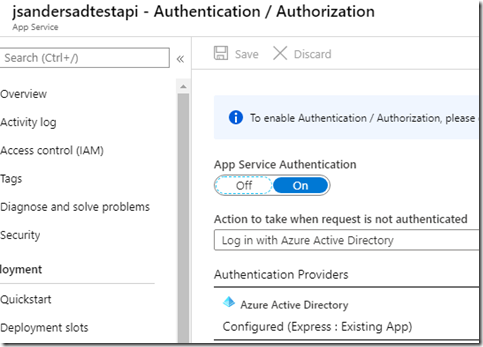
Create another resource similarly “jsandersadtestapi”
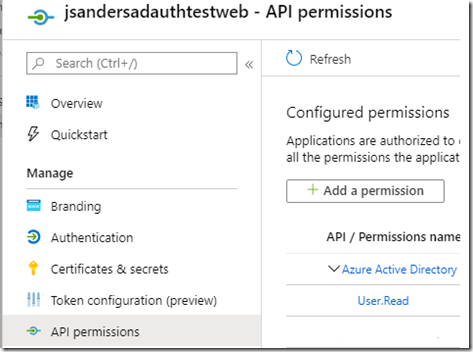
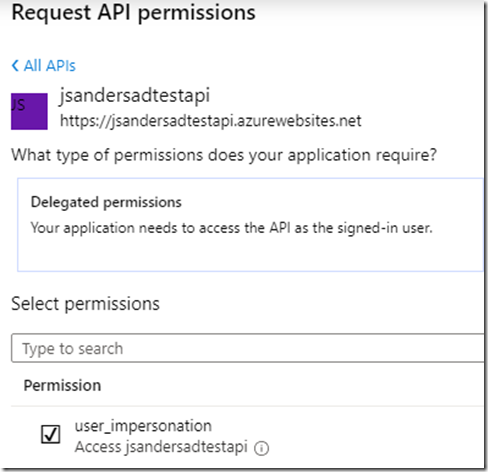
Add permissions for the first app to use user_impersonation to the api app by opening the app in Azure Active Directory,
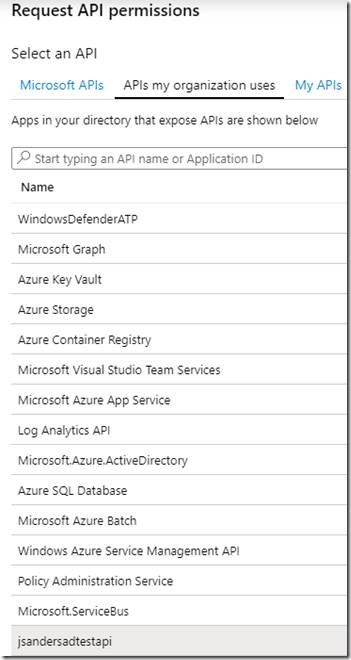
Then go to API permissions and select ‘+ Add a permission’:
Find the API app you are going to call from the Web App under ‘APIs my organization uses’ and click on it
and grant user_impersonation by selecting and hitting the ‘Add permissions’ button:
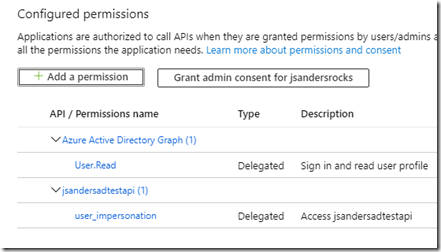
This results in Configured Permissions similar to this:
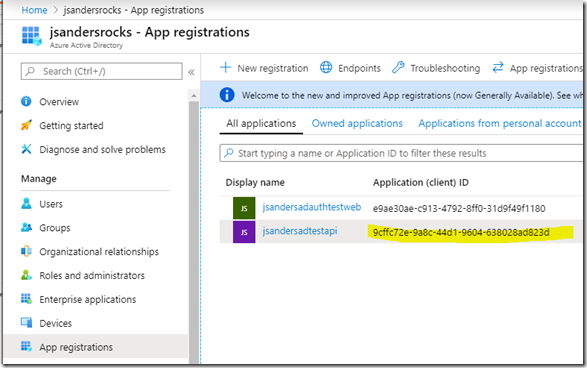
Get the Client ID of the resource you want the x-ms-token-aad-access-token to be used for (the target)
You can do this several ways but in this case I simply look it up in the Active Directory:
You will use this ID in the next step…
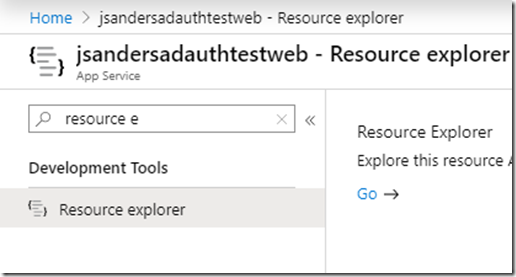
Go back to the source app “jsandersadauthtestweb” and invoke resource explorer, select ‘Go’
Click on Read/Write at the top so we can make changes:
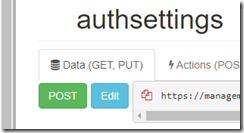
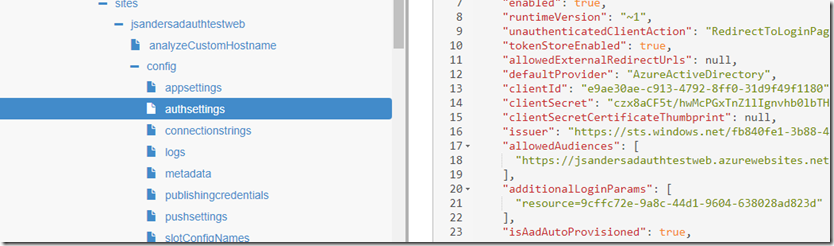
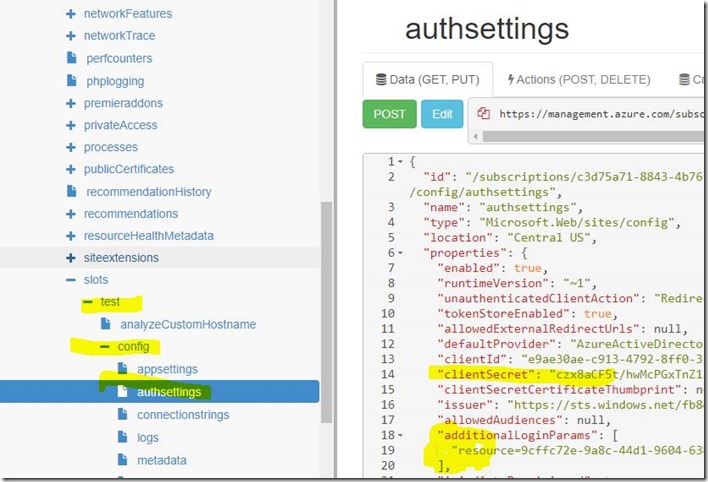
Expand the ‘config’, ‘authsettings’ section
Click on Edit:
and change the “additionalLoginParams” section from null to point to the clientid of the object you want to get a access toke for “jsandersadtestapi”
“additionalLoginParams”: [
“resource=9cffc72e-9a8c-44d1-9604-638028ad823d”
],
Click on ‘Put’ to save your changes.
I insert the following code in the web app to retrieve the auth token and display it in a Literal control I dropped on the form:
protected void Page_Load(object sender, EventArgs e)
{
try
{
// this token is a propriatary token, not a bearer token, however you can auth to another resource
// and get this as a bearer token
string accessToken = Request.Headers[“x-ms-token-aad-access-token”];
Literal1.Text = accessToken;
}
catch (Exception ex) {
Literal1.Text = “Problem with access token: ” + ex.Message;
}
}
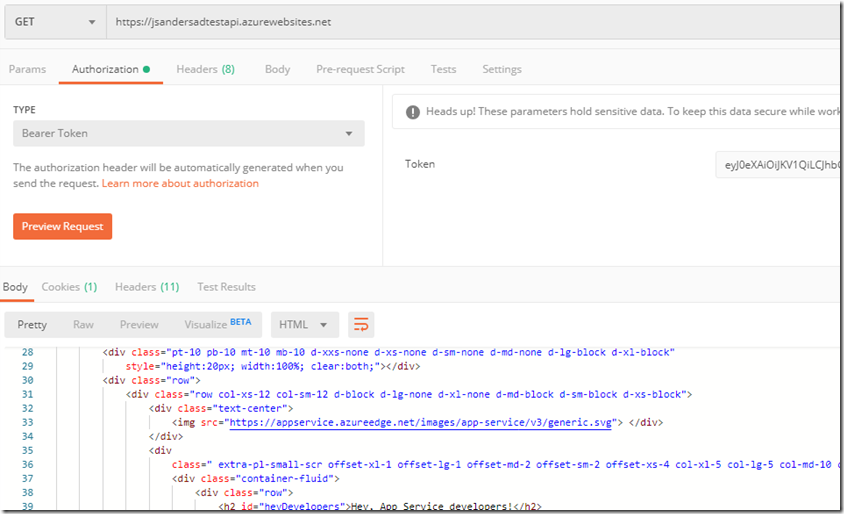
Authenticating into the app I displayed a good bearer token that I can use to authenticate to the api app (using postman below):
#
Extending to your Slots
If you want to apply this to your slots, you need to apply the same settings to the slot. Enable AD Authentication like you did for the site but ensure you choose and existing Active Directory App this time and use the one that was created for the main site.
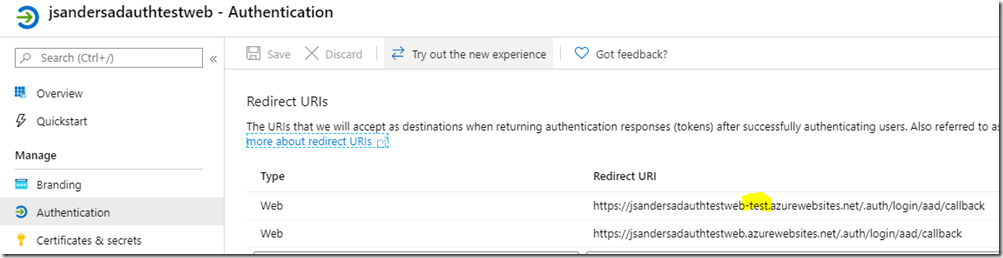
You will need to add the slot url as a valid reply url. Open the application in Active Directory and put the slot form of the reply url in and save:
After that, use resource explorer and for the new slot fill in the clientSecret and additionalLoginParams in the slots,
Troubleshooting
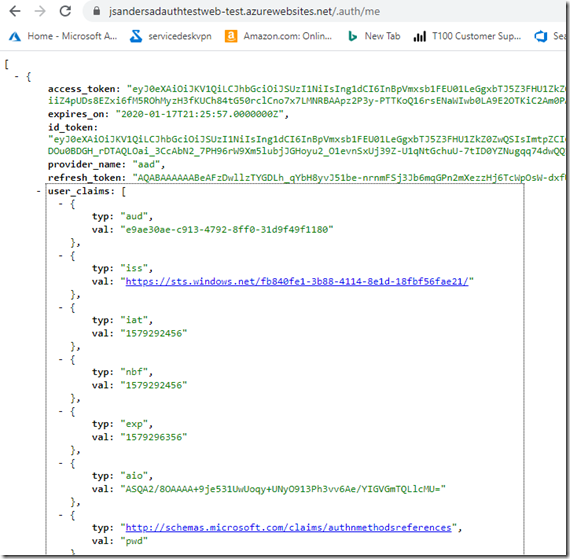
You can use the /.auth/me endpoint of your application to see these tokens and play with them:
If the token is not formed like a bearer token ‘ey….. then you forget to add the correct ‘additionalLoginParams’
If the token is blank, you don’t have the client secret set (or set correctly).
Use https://jwt.io/ to decode your token and see what it contains (note the ‘aud’) for example
Use fiddler or postman to see the auth flow!
User verbose application logging in the web app to see what Easy Auth is doing.
#
Summary
This just scratches the surface of what you can do but there was nothing ‘Easy’ out there to get you started until now.
Here is a similar post you may found enlightening as well! Azure App Service EasyAuth and Azure Active Directory Flows
Drop me a note if you find this useful!
<< Go Back